It’s a beautiful day outside and you don’t want to miss out. So you pack up your laptop and head out to your favorite neighborhood co-working space, also known as a coffee shop. Exchanging a friendly smile with your fellow co-workers, you find your desk for the afternoon, a round cafe table that is suitable for your laptop, smartphone and of course your beverage of choice.
Excited to not let the day get away, you quickly log in to your laptop and immediately start scanning for the free Wi-Fi that the coffee shop provides. With a simple click of the mouse you are connected to the internet and are ready to work.
The above scene is an everyday occurrence. Just walk into just about any coffee shop and you will encounter an array of people all working and connected to the internet. This is spreading to more than simply coffee shops, eateries, grocery stores with delis and just about any place that people congregate is now offering free Wi-Fi.
So what is the big deal?
The big deal is this thing called public Wi-Fi. To put it simply, public Wi-Fi is a wireless network that is just as it sounds…public. Anyone can get on it, which also means that anyone else on that same Wi-Fi network can see your computer. When someone can see your computer they can also, with very simple and often free tools (that can easily be downloaded from the internet), start looking at everything you

Your information can easily be stolen when connected to a public Wi-Fi
are doing. Keystrokes, emails, passwords, etc. all are open for viewing on the public Wi-Fi.
“It takes zero hacking skills to surreptitiously monitor and/or hijack communications over a public Wi-Fi network. Widely available freeware makes eavesdropping on emails and web browsing as simple as pressing a button.” -Amadou Diallo
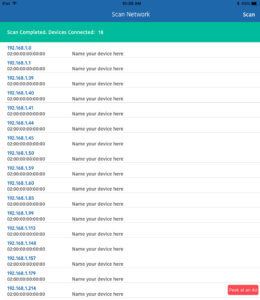
18 devices connected to the public Wi-Fi network at a local coffee shop during a slow time.
It is often very surprising to discover just how many devices are on the public Wi-fi. Just for fun, you can use a simple iPad app such as Netty to scan a network and be amazed by the number of devices connected.
Just to prove the point I walked over to a local coffee shop during one of their “slow times”. I was able to count 6 devices that could potentially be connected to the public Wi-Fi including a few laptops and smartphones. When I scanned the network with Netty, 18 devices showed up!
Every connected device is not only a potential target but also a potential hacker. When looked at that way, it is easy to see why you need to get off of the public connection!
Is it really that easy?
Yes, it is really that easy. All of your data may even be getting saved to a device you can’t even see. It may be an iPad inside of a backpack, or the person sitting outside or even in their car.
Remeber Wi-fi does not stop at the coffee shop walls, and can often be accessed for many feet away from the building.
“The proliferation of public Wi-Fi is one of the biggest threats to consumer data… a hacker can monitor the network traffic of an entire store with an iPad-sized device hidden away in his backpack.” -David Kennedy, founder of information security firm TrustedSec.
Types of hacks on public Wi-Fi
-
Sniffing:
Sniffing or snooping is pretty much just like it sounds. This is where a hacker simply grabs the data transferring over the public Wifi network.

-
Fake Hotspots:
When you connect to a wireless network named “Your Favorite Coffee Shop”, most people assume that network is owned and ran by the coffee shop. But that is not always the case. Often the bad guys will use a mobile connection, make it public and rename the network to “Your Favorite Coffee Shop”. Unknowing, patrons now connect to the network and have all their data compromised.
-
Man in the Middle Attacks (MitM):
A man in the middle attack is a bit more sophisticated, but the outcome is devastating. Essentially a hacker takes control of a part of the network and reroutes traffic to sites that look like the sites you want to go to. In reality, the site you are seeing is a spoof and the hacker collects all your data. For example, you may type in www.Amazon.com, the hacker reroutes the traffic to their own site that looks and feels like Amazon. When you log in, your credentials are captured by the hacker and the rest becomes history.
What Can I do?
The easy answer to this epidemic is to not use public Wi-fi. I can already feel the sighs of sadness as you have fallen in love with your office away from your office. But have no fear, there are solutions that can protect your data, and allow you to work out of the office.
The easiest answer for most people is the hotspot functionality on a smartphone. Both iPhone and Android devices have simple mobile

A Hotspot, such as this one from Verizon can create a secure network.
hotspot capabilities that allow you to connect to a private network (your phone) and access the internet. In addition, most phones report to you how many devices are currently connected so you can make sure it is just a single device. Keep in mind your phone will broadcast and people will be able to see your network, so make sure you are using a secure password.
In addition to smartphone hotspots, the major cellular players all offer mobile hotspots. These little devices are easy to throw in your bag and many of them can give wireless access to up to 15 devices (that have your password of course) and can be very handy when you are giving a presentation and need internet access but can’t get access to a secure wireless network.
While both of these options do have costs involved, they are not that expensive and are well worth the expense, especially when you consider the pain and suffering of giving away your bank login information, your social media accounts or sensitive company data getting hacked.
